What can I expect?
Devices – Unified Endpoint Management.
In this part of the workshop, we will take stock of the types of devices that require access to the organizational network. These include stationary or mobile endpoints such as PCs, servers, laptops, smartphones, tablets and IoT devices. The aim of this part of the workshop is to develop a concept that combines the management of stationary clients and Enterprise Mobility Management (EMM) into an all-encompassing device management concept.
Particular attention should be paid to the fact that our system only allows access to devices that are patched and secured in accordance with the guidelines
Access – Identity
Who actually accesses our network? After the devices are organized and secured, the second step is to determine whether the user is also authorized to access the network with this device. Whether to the company's own legacy apps or SaaS and web applications, access must be as easy as possible for the user in addition to the high security requirements. In this way, we prevent users from writing down passwords, sharing accesses with each other, etc. During the workshop, we will look at how accesses are currently taking place and how security is increased and acceptance is improved at the same time using modern multiple authentication and single sign-on
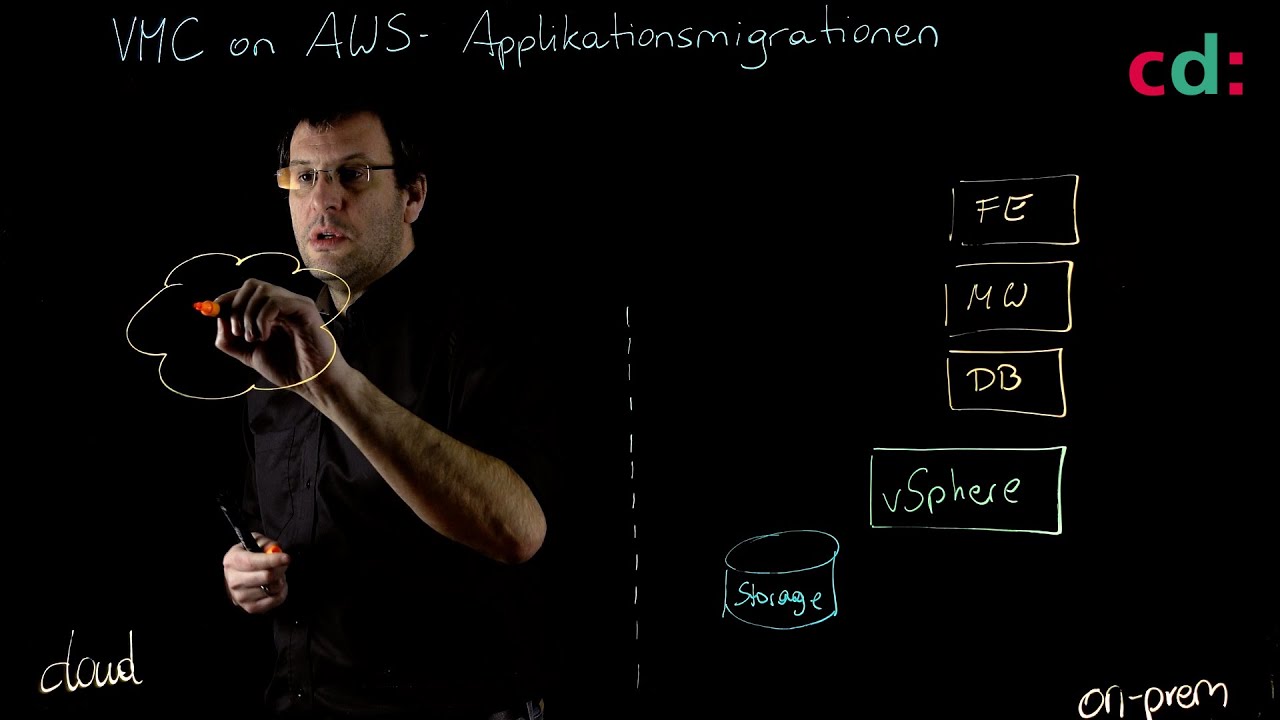
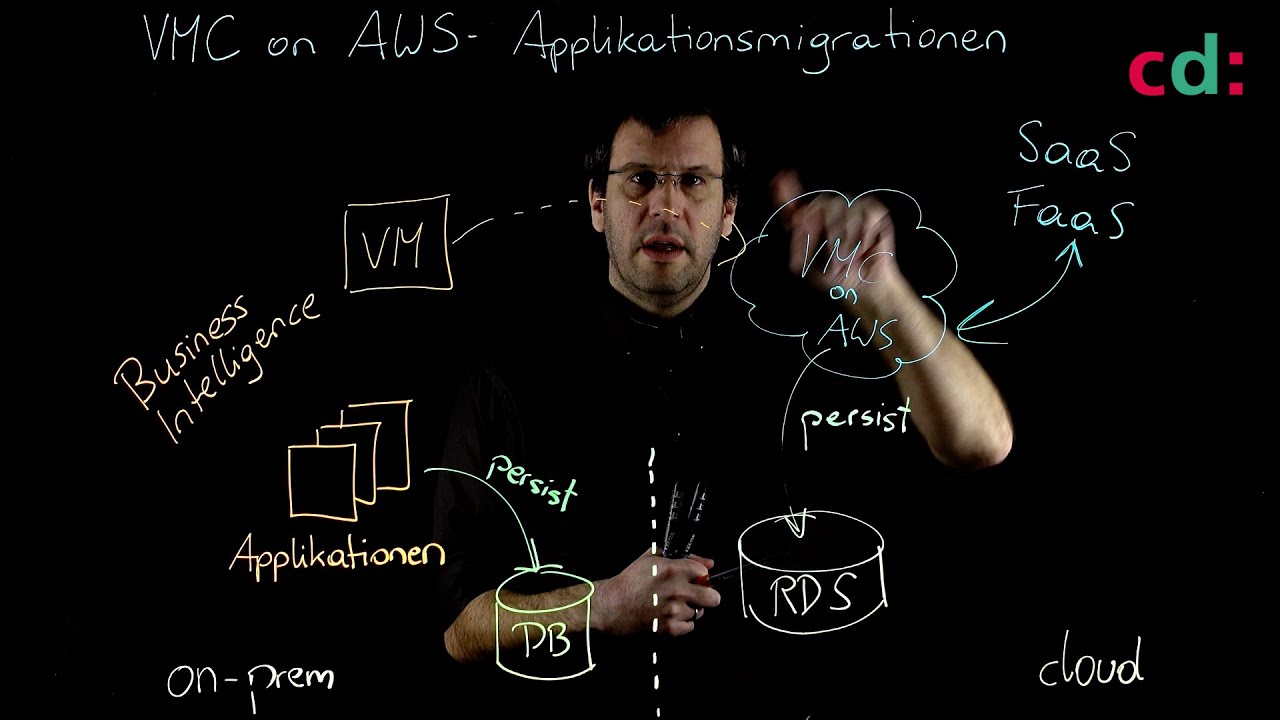
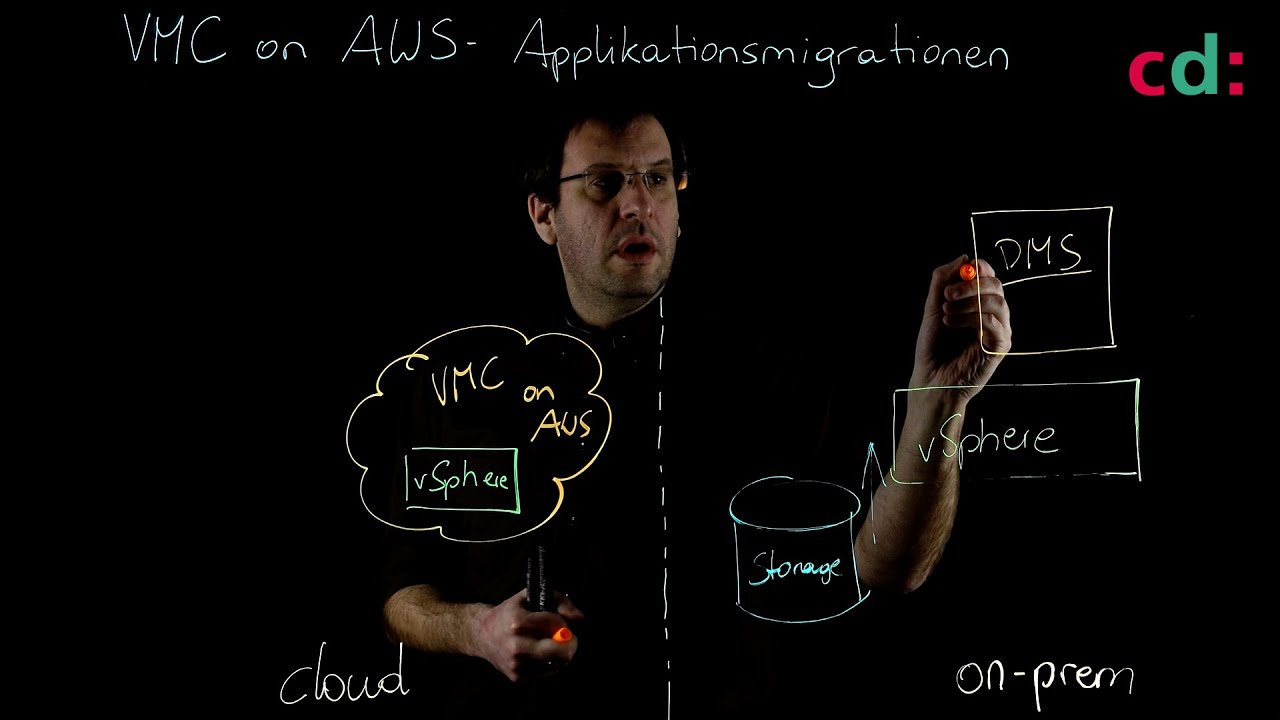
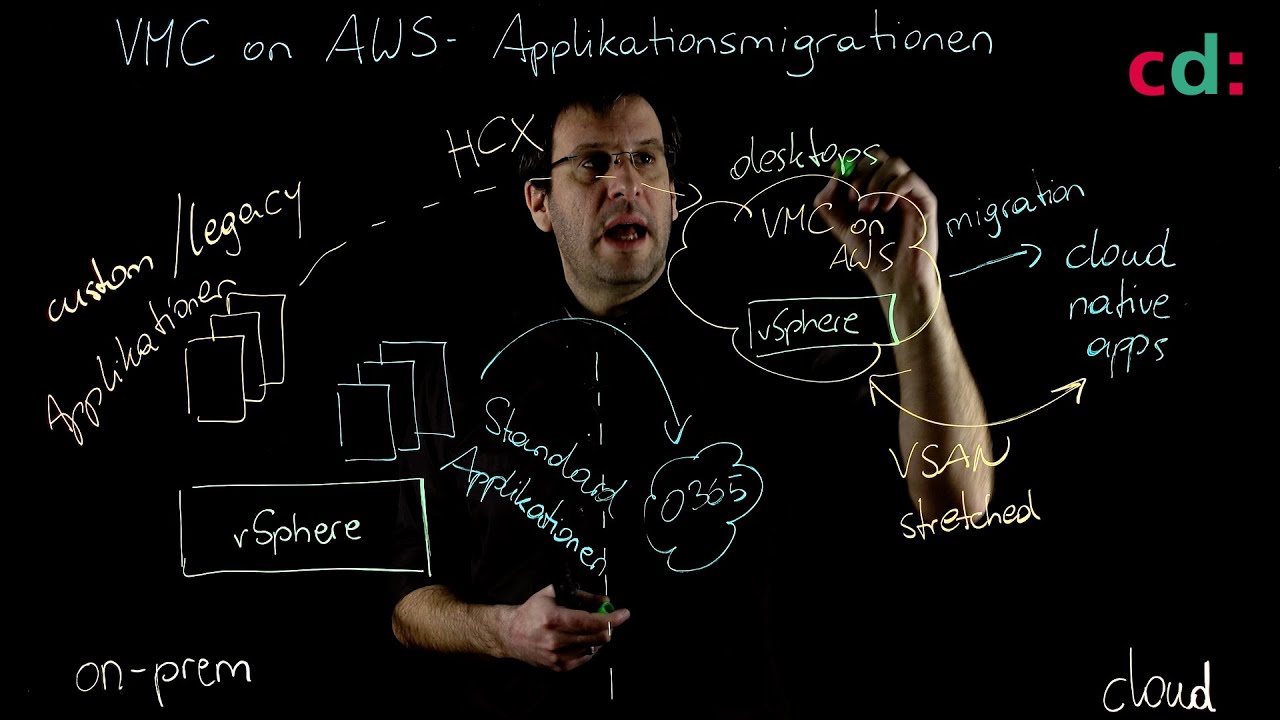
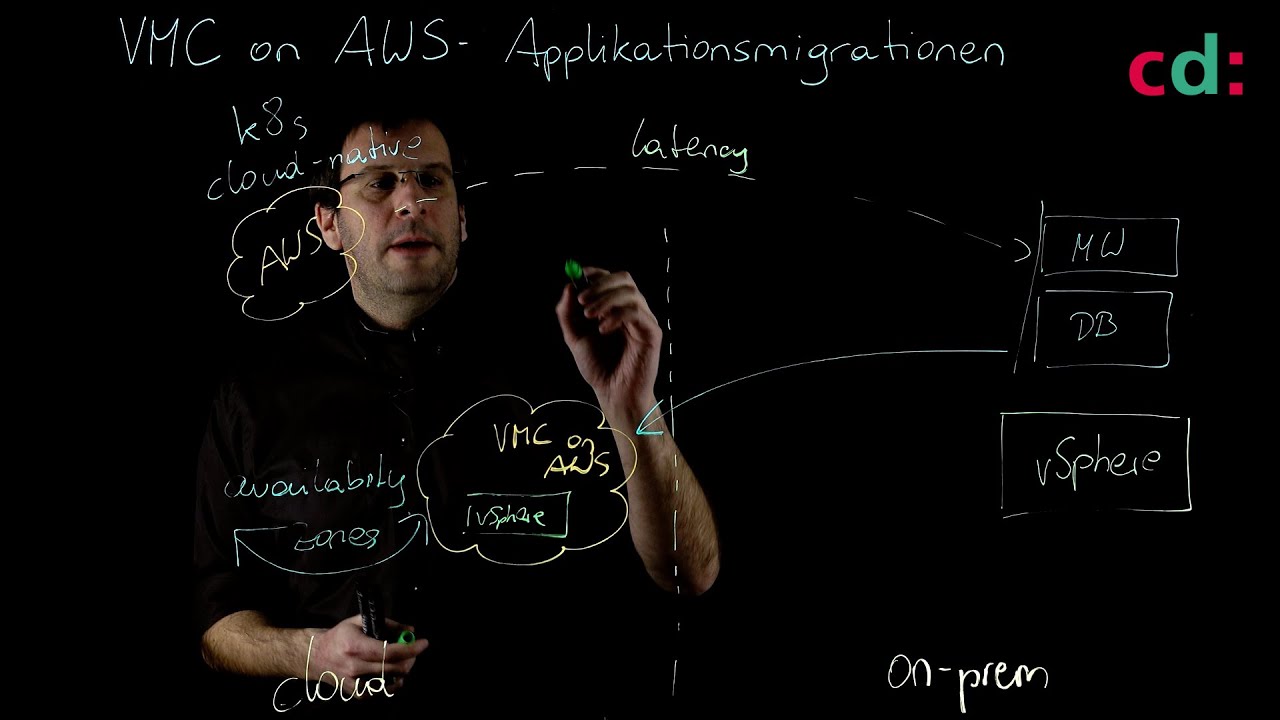
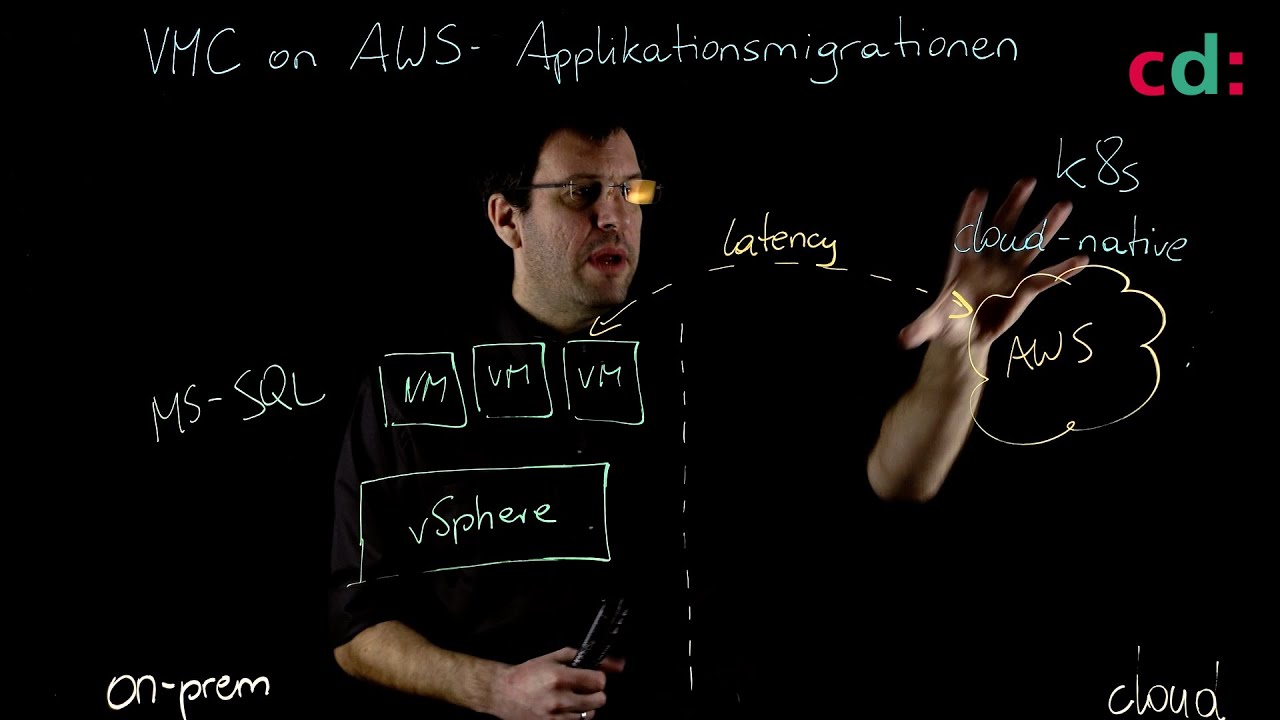
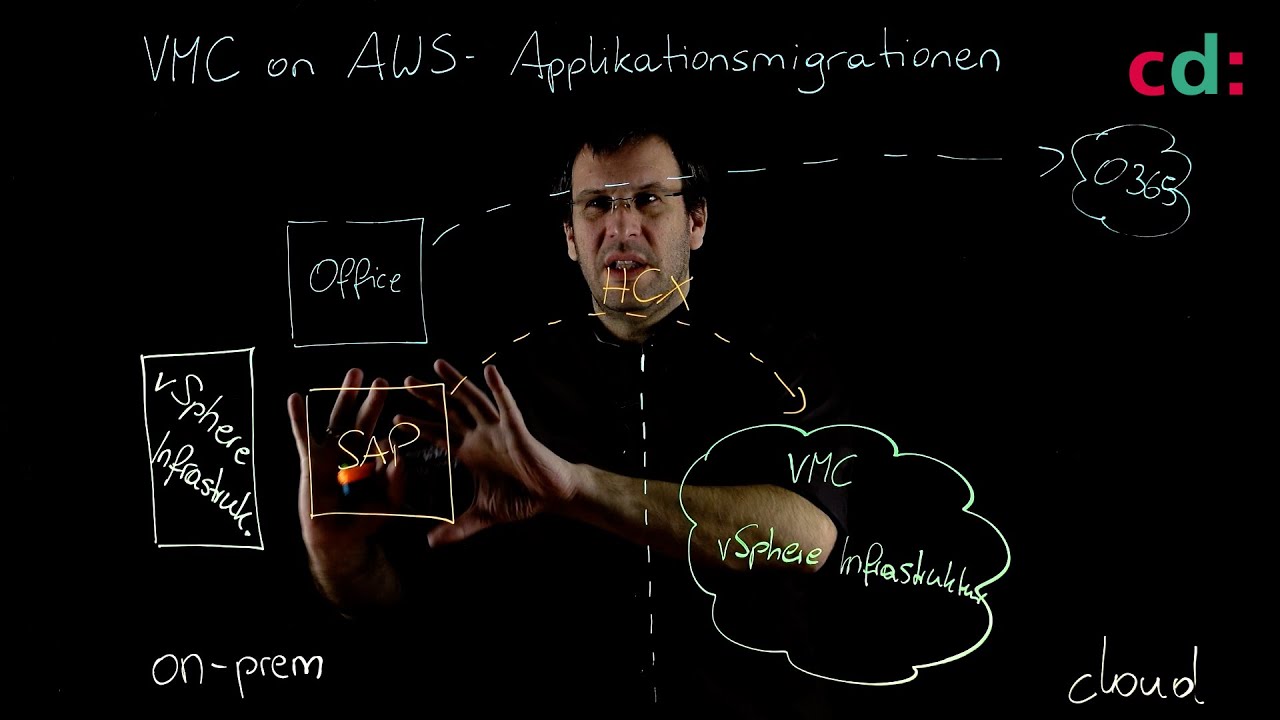
Apps – Legacy or Cloud-Native
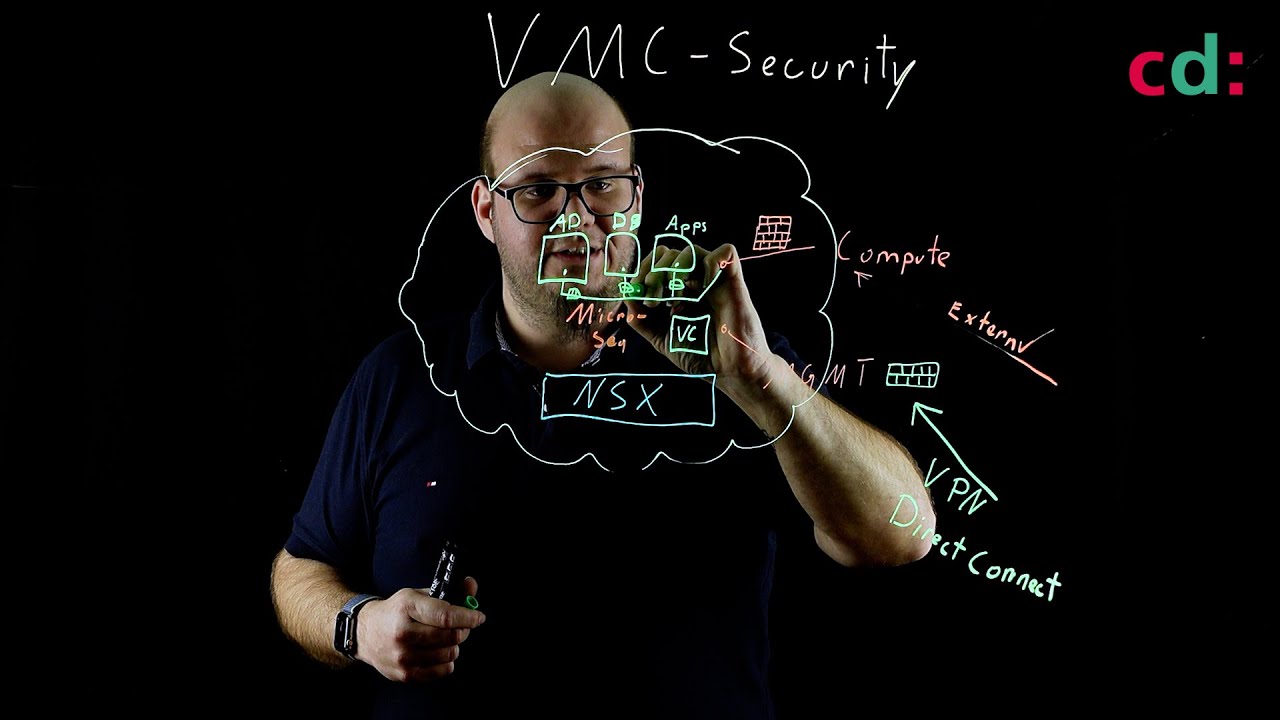
We are increasingly using cloud-hosted SaaS applications such as Microsoft Office 365. As a result, we had to say goodbye to the premise “the good guys inside, the bad guys outside”. More and more holes had to be drilled in the firewall to enable SaaS applications or to connect branches. In this part of our workshop we will deal with the question of how we can move the security perimeter to the cloud.
NextGen AV/Endpoint Detection and Response
There are three areas involved in securing endpoints and workloads:
• Hardening: How do we harden the devices in order to reduce the attack surface, i.e. how do we make them less susceptible to attacks.
• Prevention: Then we have to prevent the attacks that we cannot fight off simply by hardening.
• Detection and Response: Attacks need to be detected and we need to react to them that we cannot simply prevent.
These three areas have so far been silos, so they happen separately from each other. But they should be processes that are interconnected.
So in reality we have a whole range of tools for each area:
• Hardening: Audit and remediation or weak point management through to tools for visibility of workloads.
• Prevention: next-gen antivirus or app control or encryption
• Detection and Response: Endpoint detection and response or security analytics or forensics.
While these areas should really be connected, we buy them and implement them as separate tools with their own policy sets and consoles, and we are more concerned with the misconfiguration and misalignment of these tools than with the actual problem.